Hipaa Which of the Following Are Breach Prevention Best Practices
Which of the following are breach prevention best practices. 20 Which of the following are breach prevention best practices.

What Are The 7 Best Practices For Protecting Your Hipaa Database
A breach as defined by the DoD is broader than a HIPAA breach or breach defined by HHS.

. Answer Which of the following are breach prevention best practices. Access only the minimum amount of PHIpersonally identifiable information PII necessary. All of this above.
What are breach prevention best practices. Best practices for breach prevent are. The Health Insurance Portability and Accountability Act HIPAA Privacy Rule defines a breach as an impermissible use or disclosure of protected health.
Logoff or lock your workstation when it is unattended. Full access to over 1 million Textbook Solutions. Developing policies and procedures and implementing best practices will at the very least diminish the potential.
A- Access only the minimum amount of PHIpersonally identifiable information PII necessary. The best way to avoid being a victim of a breach is to prioritize data security. Healthcare cybersecurity breaches can be devastating but there are resources available to help you prevent cybersecurity attacks and develop best practices.
247 help from Expert Tutors on 140 subjects. HIPAA Breach Notification Rule 45 CFR 164402 A breach of PHI is presumed if unauthorized acquisition access use or disclosure of PHI occurs unless it falls into one of three exceptions. A breach as defined by the DoD is broader than a HIPAA breach or breach defined by HHS.
Best Practices in Breach Prevention - Minimizing the Risk of a Breach. How Secure is Your PHI. HIPAA Journal provides the most comprehensive coverage of HIPAA news anywhere online in addition to independent advice about HIPAA compliance and the best practices to adopt to avoid data breaches HIPAA violations and regulatory fines.
-Access only the minimum amount of PHIpersonally identifiable information PII necessary -Logoff or lock your workstation when it is unattended - Promptly retrieve documents containing PHIPHI from the printer-All of this above correct. B- Logoff or lock your workstation when it is unattended. Access to over 100 million course-specific study resources.
All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary and by promptly retrieving documents containing PHIPII from the printer. You should always logoff or lock your workstation when it is unattended for any length of time. Create a strong password policy and enforce it.
HIPAA Journal provides the most comprehensive coverage of HIPAA news anywhere online in addition to independent advice about HIPAA compliance and the best practices to adopt to avoid data breaches HIPAA violations and regulatory fines. Breaches under HIPAA and State Law HIPAA Security Rule Safeguards that Address Incident Response Plans Best Practices for Incident Response Plans The First 24 Hours Following a Breach Questions Reputation. Which of the following are breach prevention best practices.
Health Insurance Portability and Accountability Act HIPAA Create. Promptly retrieve documents containing PHIPHI from the printer. What of the following are categories for punishing violations of federal health care laws.
Best Practices in Breach Prevention Develop appropriate security measures Monitor compliance with required measures Comply with reporting requirements W. Access only the minimum amount of phipersonally identifiable information pii necessary logoff or lock your workstation when it is unattended promptly retrieve documents containing phiphi from the.
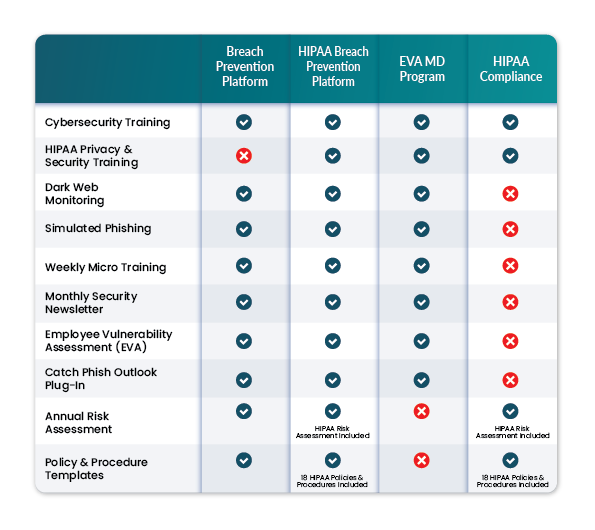
Hipaa Services Breach Secure Now
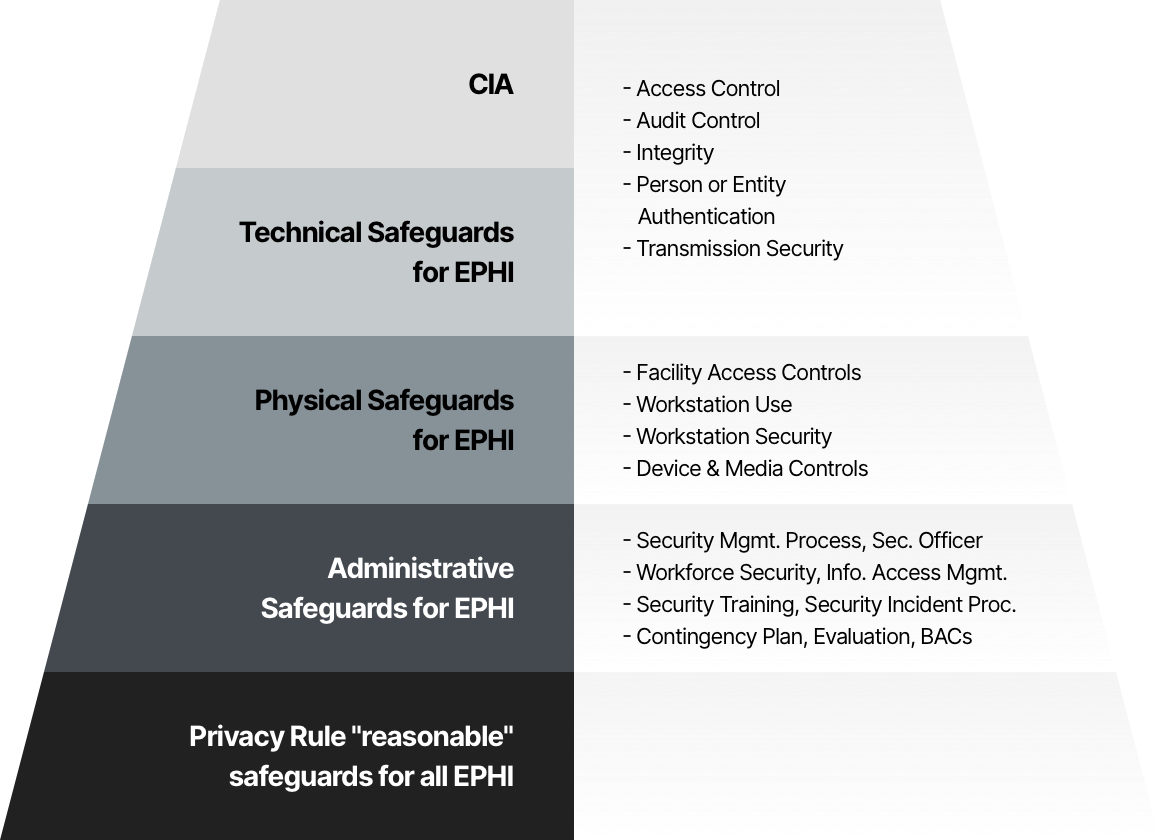
What Is Hipaa Privacy Rule Hippa Security Requirments Imperva

Preventing Hipaa Data Breaches Case Studies And Best Practices
Comments
Post a Comment